Zebra file sharing and security features
The controlled dissemination of scientific information is crucial for successful research activities in the digital age. Zebra implements file sharing and security features to provide protected access to your data via the World Wide Web for you and colleagues authorized by you.
Please note that the completed tasks (user input and the results) can be safely stored at the Zebra server for a period of one month. We reserve the right to permanently remove tasks (input and the results) which are older than one month. The cleaning usually happens on the first day of each month, e.g., all tasks submitted in January will be removed on the 1st day of March.
The following features are provided by the Zebra web-server:
- TaskID: easy access and reasonable protection of user data
- Task retraction: delete your data at any time
- HTTPS protocol: encrypt your connection and file transfer
- IP-/password-based authentication
TaskID: easy access and reasonable protection of user data
At the time of submission a new task is assigned a unique 14-symbol access code – TaskID. Assignment of a unique TaskID to each task means that loss of connection between the Zebra page and the user (e.g., the page was closed in browser or due to connection problems) neither kills the task nor deletes the data. TaskID can be used to access results on the Zebra server at any time or can be sent to a colleague to share the results. To access the results by TaskID use a corresponding form at the Zebra submission page.
Each character in the TaskID code is randomly chosen by the server from 26 lower case letters of the English alphabet and 10 numbers, making it 36 possible characters in total in each position of the 14-long string. The probability to guess a particular TaskID at random out of 6.140942e+21 possible combinations is incredibly low. Therefore, TaskID provides easy access to your results for you and authorized colleagues, while reasonably protecting your data from an unauthorized web-access by a remote user. Please note that anyone in the World Wide Web with a valid TaskID can access the corresponding task data (input data submitted by user as well as the results, produced based on this input data). It is your responsibility to protect the TaskID if the corresponding task possesses any valuable information. If you believe the TaskID has been compromised you should delete the corresponding task as soon as possible (see Task retraction below).
Task retraction: delete your data at any time
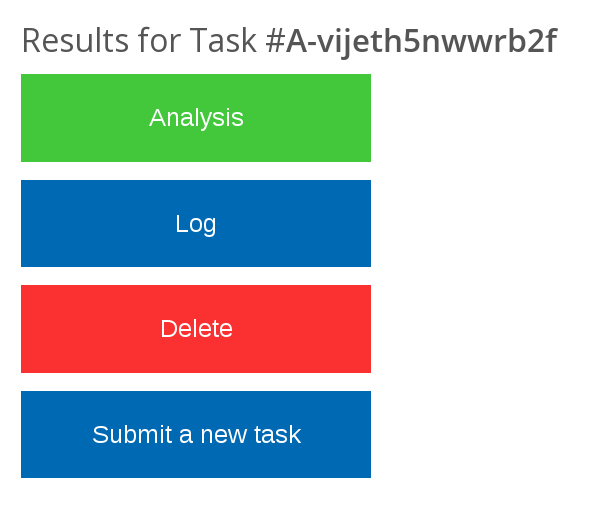
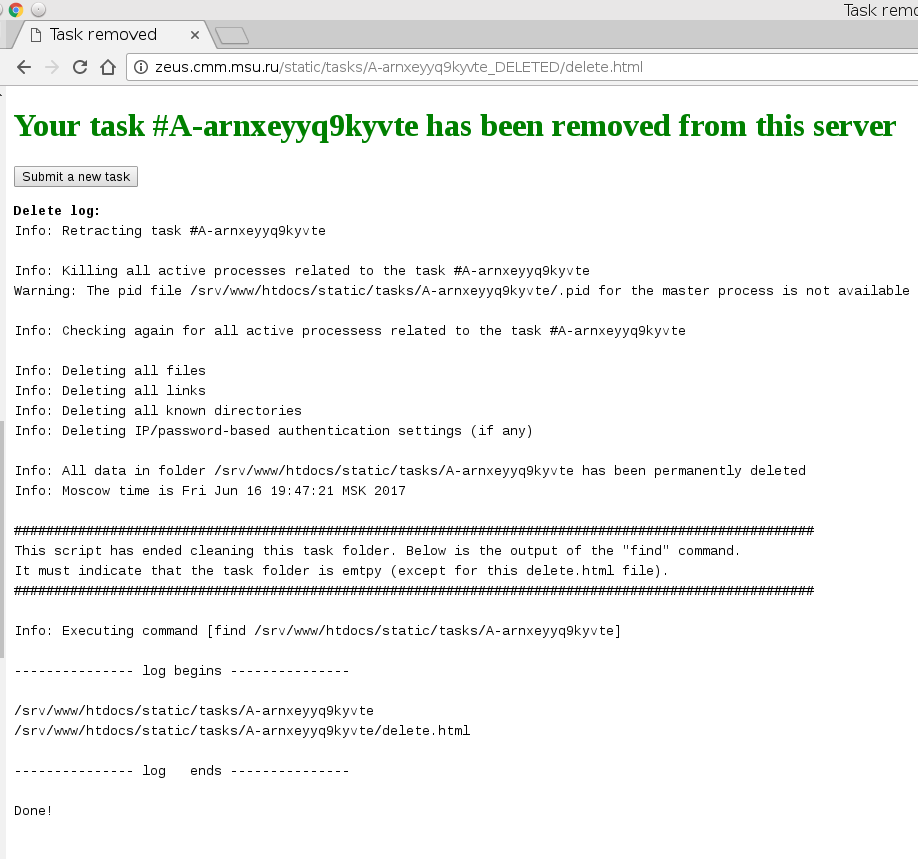
At any time you can retract your submission by pressing the "Cancel"/"Delete" button at the top of the log/results/analysis page. This will stop the task processing (or remove the task from the queue if the processing had not began) and invoke the delete script. The delete script will remove the input data as well as any intermediate data and the results that have been created. After all cleaning operations have been completed the script will execute the find command of the Linux bash shell in the task folder. This command will produce a list of all files currently in the folder. It must indicate that the task folder is empty (except for the delete.html file). The confirmation of a task retraction will be shown in the web-browser automatically (see an example below).
HTTPS protocol: encrypt your connection and file transfer
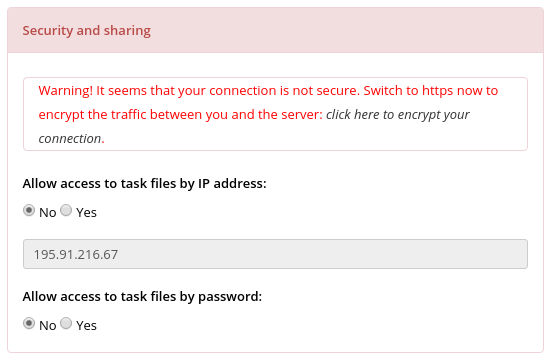
The Zebra server supports both HTTP (port 80) and HTTPS (port 443) protocols. If your connection is not encrypted (i.e., you use the HTTP version) a warning will appear at the Zebra submission page in the "Security and sharing" block (see an example above). You can encrypt your connection with the server by switching to the HTTPS protocol - click on the provided link or manually change the 'http://' prefix for 'https://' in the address line of your browser. The identity of the Zebra server is verified by Let's Encrypt Authority X3. When using the HTTPS you can click on the green lock in the address bar of your browser to learn the algorithms implemented to encrypt the connection.
IP-/password-based authentication
You can install IP-based or password-based authentication when submitting a new task to the Zebra.
To switch on the IP-based authentication simply set the radio button to "Yes" at the "Allow access to task files by IP-address" field in the "Security and Sharing" block (see the figure above). If the IP-based authentication was switched on and "Submit" button was pressed, all further access to the task files, progress log and the results would be granted only to connections from the IP which was used at the time of submission. Inability to connect to Zebra server from this IP will result in permanent disability to view the task results.
To install the password-based authentication switch the radio button to "Yes" at the "Allow access to task files by password" field in the "Security and Sharing" block (see the figure above). A password string of English letters and numbers at least 6 symbols long should be typed and re-typed in the corresponding fields. If the password-based authentication was switched on, a valid password was entered, and the "Submit" button was pressed, all further access to the task files, progress log, and the results would be granted only on entering a correct password which was set at the time of submission. Loss of the password or inability to enter it will result in permanent disability to view the task results.
Please note that IP-/password-based authentication is not required for the task retraction. This means that if IP-/password-based authentication fails - e.g., you forgot the password or can't connect to Zebra from the required IP address - you would not be able to view the task data and results but would have the power to delete them by pressing the Cancel/Delete button. This features was implemented so that the task owner always preserves the ability to remove his valuable information from the server.
Please note that the TaskID-protected access as well as the IP-/password-based authentication are features of the web-server/web-platform and therefore apply to the web-access only. While every effort is made to ensure that the input data submitted by user, the results produced from this input data, and any intermediate data are reasonably protected from any unauthorized web-access, all features described on this page are still provided "as is".